Microsoft says Lapsus$ hackers gained 'limited access' to single compromised account
In addition to Microsoft, Lapsus$ previously claimed responsibility for hacks against Okta and Nvidia
Biden warns of possible cyber attack from Russia
Rep. Darrell Issa and former deputy national security adviser KT McFarland discuss President Biden’s response to a possible cyber attack from Russia on ‘The Evening Edit.’
Microsoft revealed that the hacking group Lapsus$ was able to gain "limited access" to a single compromised account.
| Ticker | Security | Last | Change | Change % |
|---|---|---|---|---|
| MSFT | MICROSOFT CORP. | 401.14 | +7.47 | +1.90% |
The disclosure comes after Lapsus$ claimed to have exfiltrated portions of the company's source code on Tuesday. The tech giant emphasized in a blog post Tuesday evening that "no customer code or data was involved in the observed activities."
"Our cybersecurity response teams quickly engaged to remediate the compromised account and prevent further activity. Microsoft does not rely on the secrecy of code as a security measure and viewing source code does not lead to elevation of risk," the Microsoft security team said. "Our team was already investigating the compromised account based on threat intelligence when the actor publicly disclosed their intrusion. This public disclosure escalated our action allowing our team to intervene and interrupt the actor mid-operation, limiting broader impact."
According to Microsoft, Lapsus$, also known as DEV-0537, steals sensitive data from its victims, which is used for extortion. Its tactics include phone-based social engineering; SIM-swapping; accessing personal email accounts of employees; paying employees, suppliers, or business partners for access to credentials and multi-factor authentication (MFA) approval; and intruding in the crisis-communication calls and internal communications platforms of their targets.
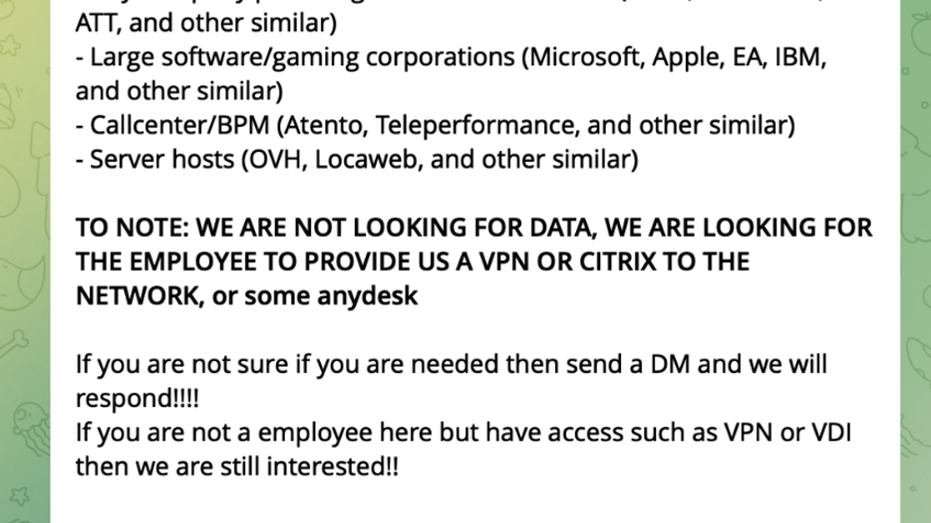
Lapsus$, also known as DEV-0537, steals sensitive data from their victims which is used to extort them for money. (Microsoft)
Microsoft says the group initially targeted organizations in the United Kingdom and South America but has since expanded to global markets. Its victims have included organizations in government, technology, telecom, media, retail, and health care sectors as well as individual user accounts at cryptocurrency exchanges.
CLICK HERE TO READ MORE ON FOX BUSINESS
In addition to Microsoft, Lapsus$ previously claimed responsibility for a cybersecurity incident that stole Nvidia employee credentials and roughly 1 terabyte of company data. It also claimed to have gained access to Okta's internal systems, though the company responded saying its systems had not been breached and remain fully operational.
Other Lapsus$ victims have reportedly included Samsung, video game giant Ubisoft, Brazil's Ministry of Health, Portuguese media group Impresa and its weekly newspaper Expresso.
| Ticker | Security | Last | Change | Change % |
|---|---|---|---|---|
| NVDA | NVIDIA CORP. | 185.41 | +13.53 | +7.87% |
| OKTA | OKTA INC. | 86.74 | +4.59 | +5.59% |
| UBSFY | UBISOFT ENTERTAINMENT SA | 0.9079 | -0.00 | -0.23% |
Recommendations by Microsoft to prevent future hacks from Lapsus$ include multi-factor authentication for all users at all locations, passwordless authentication such as Windows Hello for Business and Microsoft Authenticator and using OAuth or security asset markup language (SAML) connected to Azure AD for virtual private network (VPN) authentication.
"Microsoft continues to track DEV-0537’s activities, tactics, malware, and tools," the company said. "We will communicate any additional insights and recommendations as we investigate their actions against our customers."