Ransomware gang behind Colonial Pipeline attack, gas shortage motivated by spin and money – not politics
Hacker group called DarkSide is a criminal organization trying to spin itself as something else, experts say
Panic sets in as gas shortage slams Southeast
Arkansas Gov. Asa Hutchinson on the impact from the Colonial Pipeline cyberattack.
The ransomware gang responsible for the Colonial Pipeline attack claims it’s driven by money, not politics, and even insists it has a charitable streak.
In the wake of the devastating Colonial Pipeline cyberattack causing massive fuel shortages in parts of the U.S., DarkSide, the Russia-based ransomware gang behind the attack, has gone so far as to issue a press release stating that their organization is "apolitical."
"We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined goverment [sic] and look for other our motives," the group said in its statement.
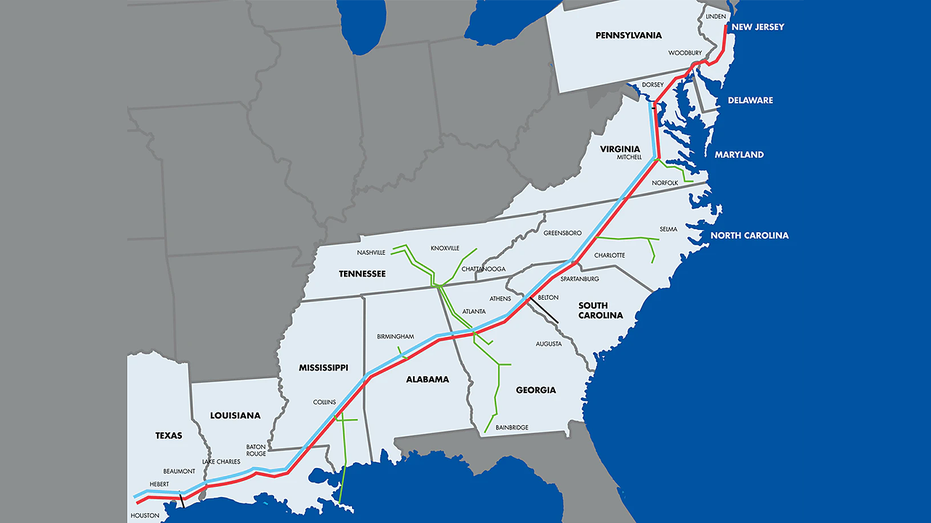
Colonial Pipeline Company connects refineries with customers and markets throughout the Southern and Eastern United States through a pipeline system that spans more than 5,500 miles between Houston, Texas and Linden, New Jersey.
TO ALLEVIATE FUEL SHORTAGES, EPA ISSUES 'EMERGENCY FUEL WAIVER' TO 12 STATES, DC
Then after proclaiming it’s just about the money, they toss in a measure of ostensible goodwill, adding, "Our goal is to make money, and not creating problems for society. From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future."
But the PR campaign appears to be little more than a weak attempt at spin by a criminal organization.
"What we are seeing is a criminal industry that normally enjoys being in the media spotlight, suddenly realizing that they made a big mistake," Lawrence Abrams, who runs the cybersecurity news site BleepingComputer, told FOX Business.
Others agree.
"The series of events playing out right now are hurting [DarkSide’s] business," Ekram Ahmed, a spokesperson for cybersecurity firm Check Point, said. "And so it appears they’ve issued a generic statement in a futile attempt to defuse the situation."
COLONIAL PIPELINE GAS SHORTAGES WIDEN: STATE-BY-STATE BREAKDOWN
And the gang has reportedly even given money to charities, including Children International and The Water Project.
Ransomware-as-a-service
DarkSide is run as a business that the cybersecurity community dubs "Ransomware-as-a-service" or RaaS. Despite its criminal implications, the term mimics other legitimate business models such as SaaS or software-as-a-service.
DarkSide is essentially two groups of people. One group is the operators and developers of the ransomware, while the other is affiliates that do the hacking and deploy the ransomware, according to BleepingComputer.
"RaaS operations are typically free-for-alls where affiliates can attack whoever they want, and the core operators simply develop the ransomware, handle negotiations and accept ransom payments," Abrams wrote.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
The DarkSide ransomware strain made its debut in the summer of 2020. And recently made an announcement of DarkSide 2.0, according to InfoSecurity Magazine.
"They claim that the Windows version of Darkside 2.0 encrypts files faster than any other ransomware-as-a-service (RaaS) and is twice as speedy as the previous iteration," the magazine reported.
And like other ransomware variants, DarkSide engages in double extortion. That typically means the criminals not only demand ransom on the encrypted data but will then threaten to make it public if a separate ransom demand is not paid, according to Krebs on Security.




















