Hackers target coronavirus stimulus checks through phishing emails
94% of COVID-19-related cyberattacks were conducted through phishing emails
Get all the latest news on coronavirus and more delivered daily to your inbox. Sign up here.
As Americans struggle to pay rent and grocery bills amid job losses related to the novel coronavirus, hackers are trying to cash in on stimulus payments.
Google said last week that in a single week in April it saw "18 million daily malware and phishing emails related to COVID-19" on top of "more than 240 million COVID-related daily spam messages."
Now, hackers are turning to relief checks to capture the attention of potential victims, according to research published Monday by cybersecurity company Check Point Research.

"For Sale By Owner" and "Closed Due to Virus" signs are displayed in the window of Images On Mack in Grosse Pointe Woods, Mich., Thursday, April 2, 2020. (AP Photo/Paul Sancya)
"In the cyber world, where there is money, there will be criminal activity," Check Point Data Team Leader Omer Dembinsky said in a statement. "As economic stimulus payments start to flow, cyber-attackers want to get their share too."
Over the past two weeks, 94 percent of COVID-19-related cyberattacks were conducted through a method called "phishing."
Phishing is when bad actors send out malicous emails that are disguised to look trustworthy with popular logos and language, usually from familiar-sounding email names, in an effort to lure victims into a trap that convinces them to share sensistive information.
Emails used subject lines such as "RE: UN COVID-19 Stimulus” and “COVID-19 Payment."
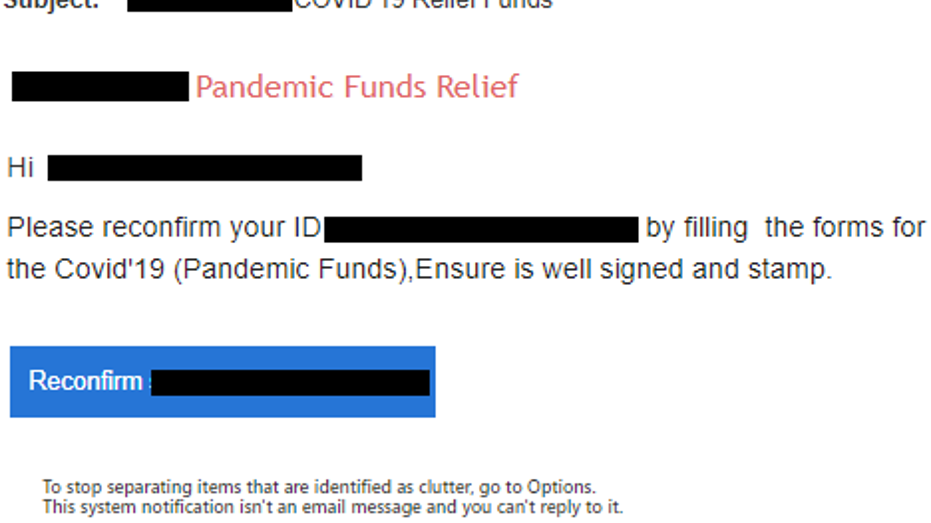
COVID-19 stimulus scam / Check Point Research
When victims open these phishing emails, they may click on links to fraudulent websites that prompt users to give up sensitive information. In the case of stimulus-related attacks, victims may give up sensitive financial information.
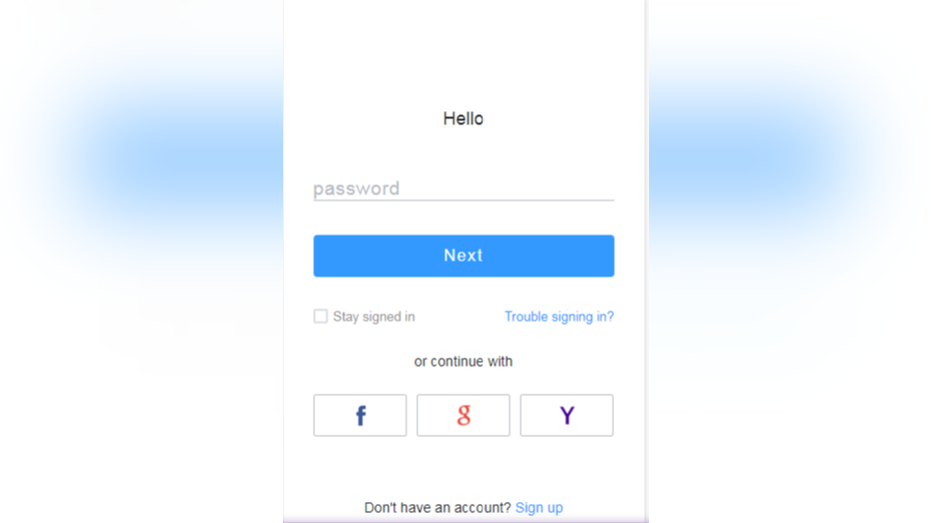
COVID-19 stimulus scam / Check Point Research
The average numer of daily cyber attacks increased by nearly six times to about 14,000 coronavirus-related cyberattacks per day compared to the previous two weeks before stimulus payments started being distributed, according to the study.
CORONAVIRUS SCAMS: A LOOK AT SCHEMES BUSTED BY THE FBI
Check Point researchers also found that since January, a total of 4,305 domains related to stimulus checks have been registered online.
Of those 4,305 domains, 2,081 were created in March, 38 of which were malicious and 583 of which were suspicious, according to Check Point. Malicious websites can do a lot of harm; they can convince potential victims to give up personal information, they can download malware onto a victim's computer without their knowledge; and they can spread false virus information.
FBI WARNS OF SCAMMERS TARGETING CORONAVIRUS FEARS
"These scam websites use the news of [COVID-19] financial incentives, and fears about coronavirus to try and trick people into using the websites or clicking on links. Users that visit these malicious domains instead of the official government websites risk having their personal information stolen and exposed, or payment theft and fraud."

A person working on a laptop in North Andover, Mass. (AP Photo/Elise Amendola, File)
To avoid these COVI-19 relief-related scams, Check Point offered a few tips. The company suggested watching out for "lookalike" domains and email addresses, or websites and addresses that are disgusied to look real but aren't. An example might be an email from or domaine called OfficialIRS.com or something similar.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
Note that the IRS website has a .gov address and all official IRS emails will be from IRS.gov.
Check Point also said people should avoid clicking on promotional links and emails. Users should conduct a web search of retailers they want to buy from before clicking on promotional links that could be malicious. Similarly, users should avoid special offers from emails and websites claiming that they are selling a $150 cure to coronavirus or something of that nature.
Additionally, the cybersecurity company recommends trying not to reuse passwords to limit the number of accounts hackers can access if they already have access to one.
CLICK HERE TO READ MORE ON FOX BUSINESS




















